Computer Icons Social Engineering Penetration Testing: Executing Social Engineering Pen Tests, Assessments and Defense, trust symbols, png | PNGWing

Social Engineering Penetration Testing: Executing Social Engineering Pen Tests, Assessments and Defense: Amazon.co.uk: Watson, Gavin, Mason, Andrew, Ackroyd, Richard: 9780124201248: Books

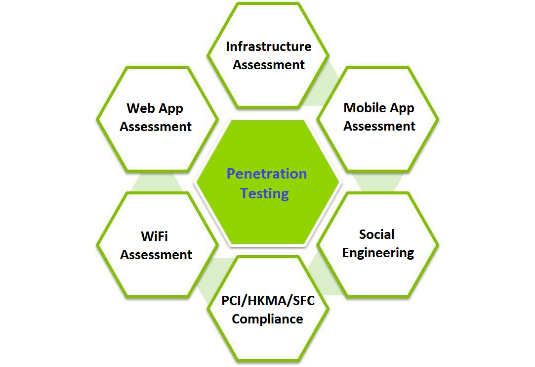
Social Engineering Penetration Testing | Managed IT Services and Cyber Security Services Company - Teceze

Social Engineering Penetration Testing | Managed IT Services and Cyber Security Services Company - Teceze

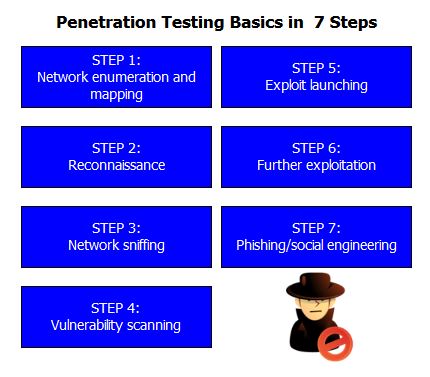
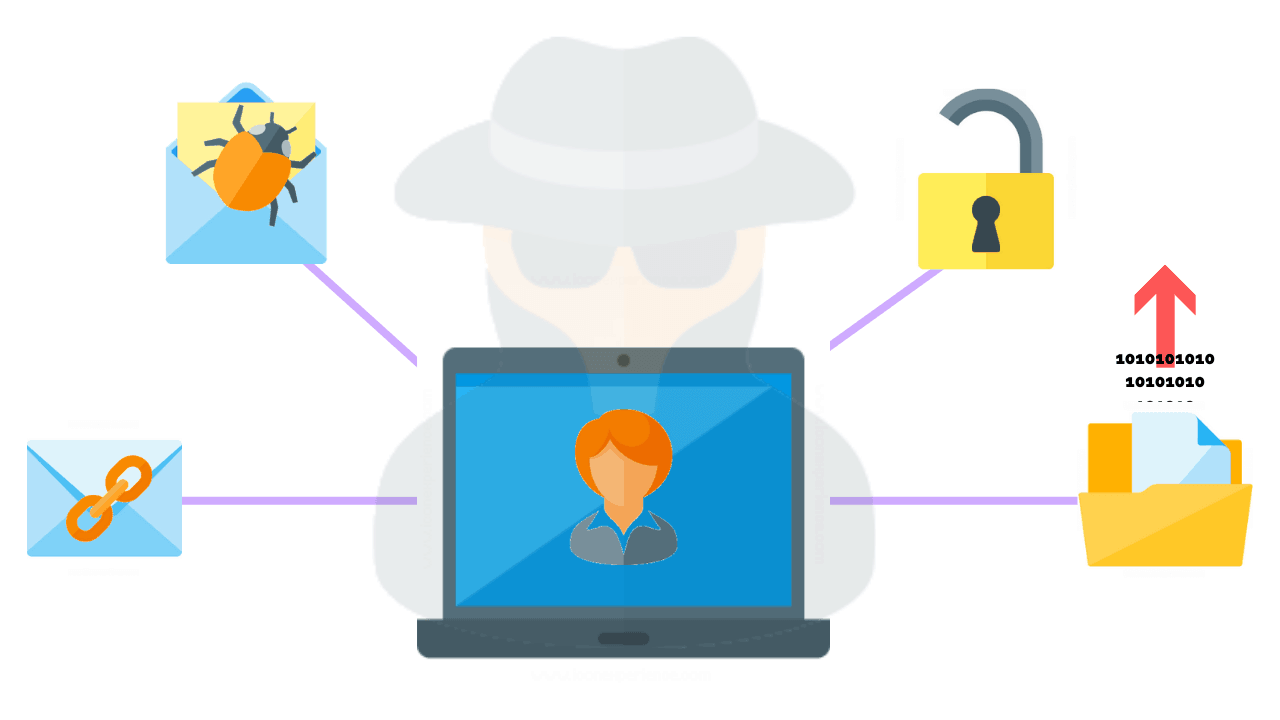
Learn Social Engineering Pen Testing with different Module – Infosavvy Cyber Security & IT Management Trainings